📌 Ultimay Security Assessment
Client: Ultimay – Cloud-Based Marketing Agency Project Management Suite
Engagement: Web Application Security Assessment
Industry: SaaS – Project Management
🛡️ Overview
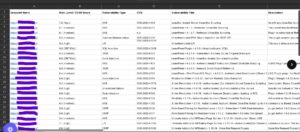
Ultimay, a cloud-based project management platform, engaged me to perform a gray box security assessment focusing on authentication, access controls, and infrastructure security. Using a Manager-level test account, I identified four critical vulnerabilities that posed significant security risks:
1️⃣ User Role IDOR – Privilege Escalation to Admin
2️⃣ User ID IDOR – Data Leak & Account Tampering
3️⃣ Remote Code Execution (RCE) via File Upload Logic Abuse
4️⃣ Stored Cross-Site Scripting (XSS) Across Multiple Modules
These findings exposed the platform to unauthorized access, account takeovers, remote code execution, and persistent client-side attacks.
🔍 Findings & Key Issues
1️⃣ Use Role IDOR – Privilege Escalation to Admin
Severity: 🔴 Critical
Issue: The platform used a hidden input field in the Edit Profile section that controlled user roles but lacked server-side validation.
Exploit: Attackers could modify their user role to admin-level privileges by simply altering the hidden role value in the request.
Impact: Full administrative access, allowing an attacker to manage users, data, and platform configurations.
Fix: Implemented strict Role-Based Access Control (RBAC) and enforced server-side validation to prevent unauthorized privilege changes.
2️⃣ User ID IDOR – Data Leak & Account Tampering
Severity: 🔴 Critical
Issue: The User ID parameter in multiple account-related endpoints allowed unauthorized access to other users’ data without authentication checks.
Exploit: Attackers could modify another user’s profile details, emails, passwords, and sensitive account settings simply by manipulating the User ID in API requests.
Impact: Mass account compromise, leading to data leaks, identity fraud, and platform-wide security failures.
Fix: Enforced server-side authorization checks to ensure users can only access and modify their own data.
3️⃣ Remote Code Execution (RCE) via File Upload Logic Abuse
Severity: 🔴 Critical
Issue: The file upload feature accepted arbitrary file types, storing them locally before pushing them to AWS S3.
Exploit: Attackers could upload malicious PHP files, bypass upload restrictions, and execute commands on the server via the /uploads/temp/ directory.
Impact: Full remote shell access, enabling attackers to exfiltrate data, manipulate databases, and escalate system privileges.
Fixes:
✅ Restricted file types to only allow approved formats.
✅ Disabled execution permissions in upload directories (chmod -x).
✅ Moved temporary files to a non-public directory before processing.
4️⃣ Stored Cross-Site Scripting (XSS) Across Multiple Modules
Severity: 🔴 Critical
Issue: Multiple input fields across 12+ modules failed to sanitize user inputs, leading to persistent JavaScript injection.
Exploit: Attackers could inject malicious scripts that executed when users viewed affected pages, enabling:
- Session hijacking (stealing authentication cookies).
- Phishing attacks (injecting fake login prompts).
- Data theft & account compromise (stealing form inputs).
Affected Modules: - Daily Reminders, Prospects, Customers, Proposals, Vendors, Projects, Files, Invoices, Billing, and more.
Remediation Process: - Initial Fix: Applied output encoding and input sanitization (
strip_tags,htmlspecialchars). - Long-Term Collaboration: Worked closely with Ultimay’s developers to validate fixes across all affected areas.
- Final Validation: Conducted follow-up testing to ensure full XSS mitigation.
📢 Outcome
✅ Enforced secure role-based access controls (RBAC), preventing privilege escalation.
✅ Eliminated user ID-based data leaks, securing account integrity.
✅ Hardened infrastructure security, blocking RCE & unauthorized file executions.
✅ Successfully mitigated stored XSS risks, ensuring long-term protection.
✅ Validated all fixes post-remediation, securing Ultimay’s platform against future exploits.